Auto-Provisioning Users with SAML 2.0 Integration
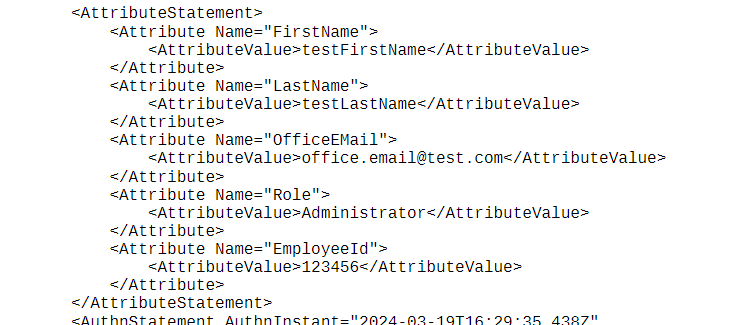
SAML 2.0 integration enhances the existing Single Sign-On (SSO) workflow to provide automated user provisioning and role assignment support in Enterprise Archive. This simplifies the user management process, strengthens security, and reduces manual work for administrators. This functionality relies on user information about each employee being passed as attributes within the SAML assertion issued by the customer's Identity Provider (IDP). The following user information needs to be passed as attributes within the SAML token:
|
Fields |
Description |
Attribute Name |
|
First Name |
User's first name |
FirstName |
|
Last Name |
User's last name |
LastName |
|
Email ID |
User's primary email address |
OfficeEMail |
|
Role |
User's assigned role within Enterprise Archive |
Role |
|
Employee ID |
Unique identifier for the user within the customer's system |
EmployeeId |
To automate how users are added to the system, a feature flag has been introduced. This flag controls whether user provisioning happens automatically during the SSO login process.
If Enabled: New employees attempting to log in for the first time will be automatically created as users in Enterprise Archive and assigned the appropriate role. Additionally, existing SSO users with role changes reflected in the SAML assertion will have their roles updated within Enterprise Archive.
If Disabled (Default): Employees who already exist as SSO users in Enterprise Archive will be able to log in normally.
Contact Smarsh Support to enable this feature.
Configuring your Identity Provider for Single Sign-On
SSO allows users to sign in once to their IDP and access the Enterprise Archive server without having to enter their credentials again. To enable single sign-on for Enterprise Archive, the IDP server should be configured with the following:
SAML Assertion Endpoint: This is the web address (URL) where your IDP will send a special security token containing user information. This token is called a SAML assertion, and it allows the Enterprise Archive server to identify the user without requiring them to sign in again.
Entity ID (Enterprise Archive Server Identifier): This is a unique identifier that tells your IDP exactly which server (the Enterprise Archive server) it needs to communicate with using SAML.
Required User Attributes: These are the list of attributes required to provision the users in Enterprise Archive. Your IDP needs to be configured to include these details in the SAML assertion. The required attributes are:
First Name
Last Name
Office Email Address
User Role
Employee ID
User Role Change
The proposed enhancement to automate user provisioning with SSO streamlines user management within the Enterprise Application. New users will be automatically assigned roles based on the information in the IDP's SAML assertion. Additionally, any role changes made within the IDP will be synchronized with Enterprise Archive during the user's next login, ensuring users always have the correct access permissions.
Revoking User Access with SSO
To revoke a user's access to Enterprise Application via SSO, a two-step process is required. First, the Enterprise Archive administrator needs to create a new user role that removes all access privileges. This restricted role should then be assigned to the user in the IDP system. When the user attempts to log in, Enterprise Archive will detect the restricted role designation within the SAML assertion sent by IDP and deny access.