Configuring Single Sign-On
Single Sign-on (SSO) allows you to configure the single sign-on parameters in Enterprise Archive to communicate with the third-party tool that is used to manage the active directory details of the client.
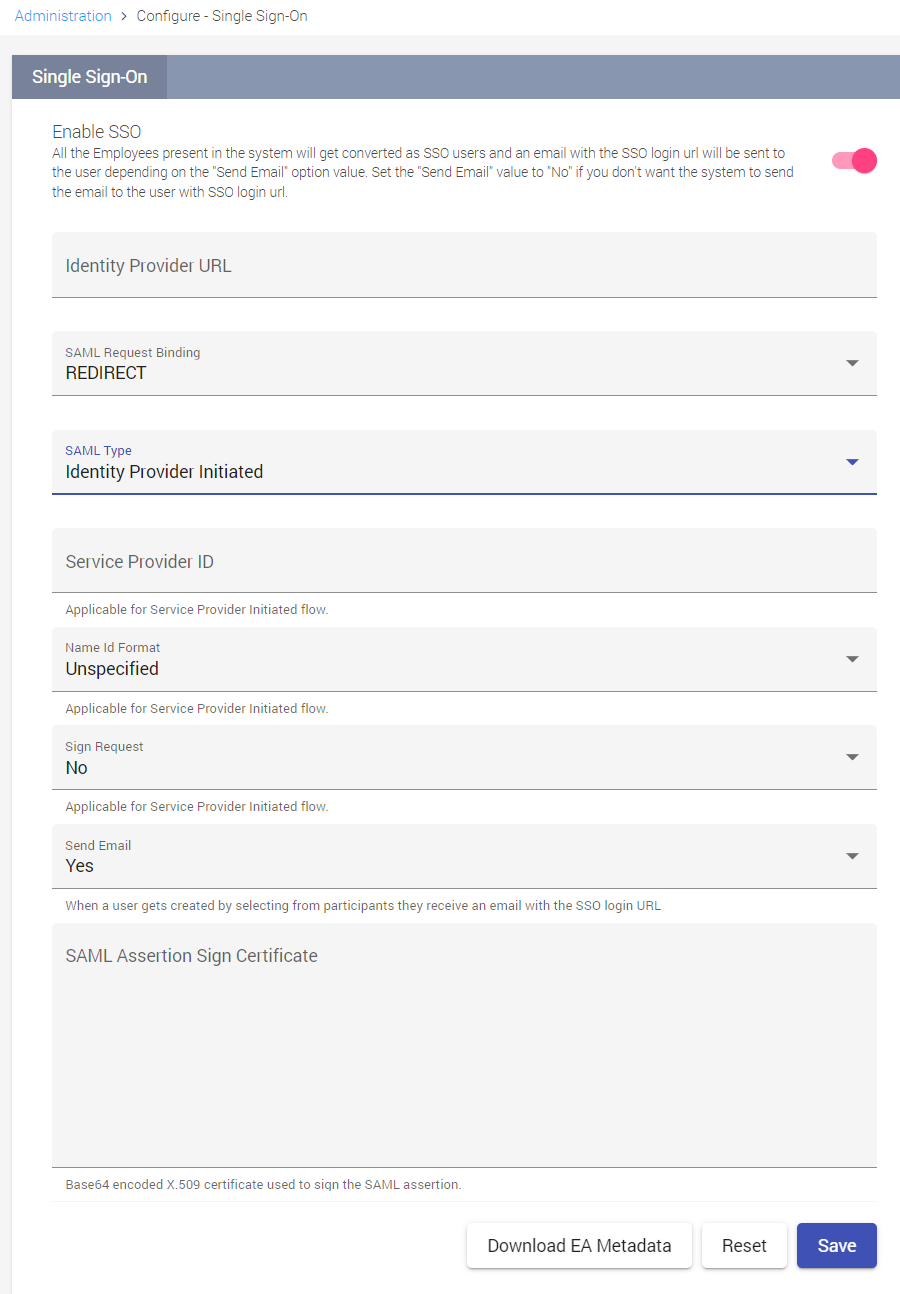
To configure SSO, enable the Enable SSO check box. All the Employees present in the system are converted as SSO users and an email with the SSO login url will be sent to the user depending on the set Send Email value. Set the Send Email value to No if you don't want the system to send the email to the user with SSO login url.
Once SSO is enabled, configure the following fields:
|
Fields |
Description |
|
Identity Provider URL |
The URL of the single sign-on service provider. |
|
SAML Request Binding |
Choose Redirect or Post for Identity Provider Initiated SAML Type. Choose Post for Service Provider Initiated SAML Type. |
|
SAML Type |
Choose one of the following SAML type according to your network preference:
For further SAML configuration, see SAML Configuration. |
|
Service Provider ID |
The Service Provider ID will be auto-populated once the service provider has been configured. This can be updated based on your configuration. |
|
Name ID Format |
The Name ID format must be one of the following:
|
|
Sign Request |
The sign request can be Yes or No as per your configuration. |
|
Send Email |
If set to Yes, an email will be triggered to those users created by importing participants. |
|
SAML Assertion Sign Certificate |
Add the SAML assertion certificate that is available in the IDP metadata. |
|
Download EA Metadata |
To generate and download SAML metadata to your system locally. Optionally, you can generate the metadata without logging into the Enterprise Archive application. |
Generating Enterprise Archive Metadata without logging into Enterprise Archive
To generate EA Metadata without logging into Enterprise Archive application or t o configure the API endpoint in the IDP server , invoke the following URL:
https://<tenant url>/cxf/saml20/eametadata.
Ensure that the Enterprise Archive tenant is up and running.
SAML Configuration
Security Assertion Markup Language (SAML) is an XML-based, open-standard data format for exchanging authentication and authorization data between an identity provider and a service provider. Enterprise Archive acts as a Service Provider and the server that generates SAML token acts as an Identity Provider.
You must configure Enterprise Archive with one of the SAML configurations types:
Identity Provider Initiated (IDP)
A server that performs the authentication, generates SAML assertion and send it to Service Provider.
Normally this tool is hosted in customer premise.
IDP Metadata will be shared by customers to Smarsh that contains the following parameters:
|
Parameters in IDP Metadata |
Description and Example |
|
SingleSignOnService → Location |
Defines the IDP End point URL to which Enterprise Archive will send the SAML request. Sample entry from IDP Metadata: <md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://<URL>"/> Here, Identity Provider URL will be https://<URl> |
|
SingleSignOnService → Binding |
Defines the HTTP method of sending SAML request. Sample entry from IDP Metadata: <md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-REDIRECT" Location="https://<URL>"/> Here the SAML Request Binding will be Redirect |
|
IDPSSODescriptor → WantAuthnRequestsSigned |
Defines if the SAML request should be signed or not. Value must be either true or false. Sample entry from IDP Metadata: <md:IDPSSODescriptor WantAuthnRequestsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> Here the Sign Request will be Yes. |
|
<md:KeyDescriptor use="signing"> → X509Certificate |
The certificate used to sign the SAML assertion. This will be a base64 encoded string value. |
|
NameIDFormat |
List of Name ID Format expected by IDP in the SAML request sent by the Service Provider. |
Service Provider Initiated (SP)
A SAML service provider is a system entity that receives and accepts an authentication assertion issued by a SAML identity provider. In this case, Enterprise Archive will act as Service Provider.
SP metadata will be shared by Smarsh to customers that contains the following parameters:
|
Paramters in SP Metadata |
Description and Example |
|
AssertionConsumerService → Location |
Defines the end point exposed in Enterprise Archive to receive SAML response. Sample entry from SP metadata: <md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://indevalcz.smarsh.net/portola/cxf/auth/ssoLogin" index="1"/> The location value must be constructed according to tenant URL. Here indevalcz is the tenant name. |
|
<md:KeyDescriptor use="signing"> → X509Certificate |
The certificate will be stored in the system and corresponding values must be configured in the Enterprise Archive server properties. Public key of the certificate must be provided in the SP metadata. Contact Smarsh Representative to configure the server properties. |
|
EntityDescriptor → entityID |
This is the ID for SP server. Sample entry from SP metadata: <md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" validUntil="2018-02-07T12:12:29Z" cacheDuration="PT604800S" entityID="demo1.smarsh.net"> Here, the Service Provider ID will be demo1.smarsh.net This value can be any string value. Not required to be tenant name. |
|
NameIDFormat |
Name ID Format that is sent as part of SAML request. The value must be one of the Name ID Format value present in the IDP metadata. |